Intercepting Mobile Calls: A Deep Dive into Threats to National Security
/cdn3.vox-cdn.com/uploads/chorus_asset/file/675728/phones.0.jpg)
Intercepting Mobile Calls: A Deep Dive into Threats to National Security
Introduction
In today’s interconnected world, mobile communication has become the backbone of personal and professional interactions. As mobile networks evolve from 2G to 5G, the need for secure communication channels has never been more critical. However, with advancements in technology, the risk of mobile call interception has also increased, posing significant threats to national security. This blog post explores the technical aspects of mobile call interception, the methods used by malicious actors, and the profound implications these have on national security.
"No system on the internet is entirely secure." - Bhaskarvilles
1. The Evolution of Mobile Communication Networks
Mobile communication has evolved significantly over the past few decades, from simple voice calls to sophisticated data transfer, video calls, and internet browsing. Understanding the evolution of mobile communication networks is essential to grasp the vulnerabilities that exist in each generation of technology.

1.1 GSM (2G) Networks
The Global System for Mobile Communications (GSM), introduced in the early 1990s, was the first digital mobile communication system that gained widespread adoption. While GSM brought numerous advantages over analog systems, it also introduced security vulnerabilities that allowed for call interception.
-
Architecture: GSM uses a combination of Time Division Multiple Access (TDMA) and Frequency Division Multiple Access (FDMA) to separate voice channels. The communication between the mobile device and the base station is encrypted using the A5/1 and A5/2 algorithms. However, these encryption methods have been proven to be weak and susceptible to brute-force attacks.
-
Vulnerabilities: The primary vulnerabilities in GSM networks stem from the weak encryption algorithms and the use of Signaling System No. 7 (SS7) for network interoperability. SS7, despite its critical role in mobile networks, lacks robust security measures, making it a prime target for interception.

1.2 UMTS (3G) Networks
The Universal Mobile Telecommunications System (UMTS) was introduced to address the security flaws in GSM networks. UMTS uses stronger encryption algorithms and a more secure authentication process, but it still has its share of vulnerabilities.
-
Improved Security: UMTS introduced the KASUMI encryption algorithm, which was designed to be more secure than A5/1 and A5/2. The authentication process in UMTS is also more robust, involving mutual authentication between the mobile device and the network.
-
Vulnerabilities: Despite these improvements, UMTS is not immune to interception. The backward compatibility with GSM networks means that attackers can force a mobile device to downgrade to GSM, where the encryption is weaker, making interception easier.
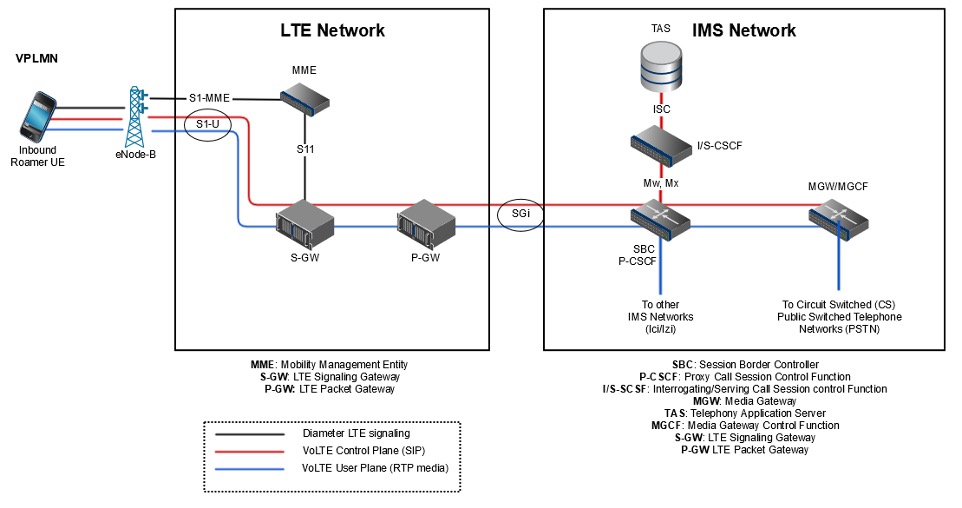
1.3 LTE (4G) Networks
Long-Term Evolution (LTE) networks brought significant improvements in speed and security. LTE uses the Diameter protocol instead of SS7 and employs strong encryption algorithms like AES (Advanced Encryption Standard).
-
Enhanced Security: LTE's security framework is based on the Evolved Packet System (EPS) and includes features like Non-Access Stratum (NAS) encryption and integrity protection. These features make LTE more secure than its predecessors.
-
Vulnerabilities: While LTE is more secure, it is still vulnerable to certain types of attacks, such as IMSI catching and man-in-the-middle (MITM) attacks. The Diameter protocol, although more secure than SS7, has its own set of vulnerabilities that can be exploited for interception.
1.4 5G Networks
The fifth generation of mobile networks, 5G, promises even greater security features along with faster speeds and lower latency. 5G introduces new encryption algorithms and a more complex network architecture.
-
Advanced Security: 5G networks use the 256-bit AES encryption algorithm and have improved mutual authentication processes. The introduction of network slicing and software-defined networking (SDN) adds layers of security to the network.
-
Potential Vulnerabilities: Despite these advancements, 5G is not foolproof. The complexity of 5G networks introduces new attack vectors, such as vulnerabilities in network slicing and SDN components. Additionally, the backward compatibility with 4G and 3G networks means that older vulnerabilities could still be exploited.
2. Technical Background: Key Communication Protocols
To understand how mobile call interception occurs, it's essential to delve into the communication protocols that govern mobile networks. These protocols are the backbone of mobile communication, and their vulnerabilities can be exploited by malicious actors.
2.1 SS7 Protocol
Signaling System No. 7 (SS7) is a set of telephony signaling protocols used to set up and tear down telephone calls in most of the world's public switched telephone networks (PSTN). Despite being a crucial component of mobile networks, SS7 is inherently insecure.
-
SS7 Vulnerabilities: SS7 was designed in the 1970s when security was not a primary concern. As a result, it lacks robust authentication mechanisms, making it susceptible to various attacks, including eavesdropping, SMS interception, and call forwarding.
-
Exploitation for Interception: Attackers can exploit SS7 vulnerabilities by gaining unauthorized access to the SS7 network. This allows them to intercept calls and SMS messages, track the location of mobile users, and even redirect calls to other numbers.
2.2 Diameter Protocol
The Diameter protocol was introduced as a replacement for SS7 in 4G networks. It is used for authentication, authorization, and accounting (AAA) in LTE and 5G networks.
-
Security Features: Diameter includes several security features, such as support for IPsec and TLS for securing communication between nodes. However, it also has its vulnerabilities.
-
Vulnerabilities: Diameter's complexity and the need for backward compatibility with SS7 mean that it can still be exploited for interception. Attackers can manipulate the protocol to perform MITM attacks, reroute traffic, or cause denial-of-service (DoS) attacks.
2.3 SIP and VoIP Protocols
The Session Initiation Protocol (SIP) is widely used for initiating, maintaining, and terminating real-time sessions, such as voice and video calls over IP networks. VoIP (Voice over IP) uses SIP for call setup and teardown.
-
SIP Vulnerabilities: SIP is susceptible to several types of attacks, including SIP hijacking, where an attacker takes control of a session, and MITM attacks, where an attacker intercepts the communication.
-
Interception Techniques: Attackers can exploit SIP vulnerabilities to intercept VoIP calls, manipulate call data, or impersonate participants in the call. These attacks can be particularly dangerous in environments where VoIP is used for sensitive communications.
3. Methods of Mobile Call Interception
Mobile call interception can be achieved through various methods, each exploiting different vulnerabilities in the communication network. In this section, we will explore some of the most common and advanced interception techniques.
3.1 IMSI Catchers (Stingrays)
IMSI catchers, commonly known as Stingrays, are devices that mimic legitimate cell towers to intercept mobile communications. They are widely used by law enforcement agencies, but they can also be used by malicious actors.
-
How IMSI Catchers Work: IMSI catchers work by broadcasting a stronger signal than nearby legitimate cell towers, tricking mobile devices into connecting to them. Once connected, the IMSI catcher can intercept calls, SMS messages, and other data.
-
Detection and Countermeasures: Detecting IMSI catchers is challenging because they operate in a way that is similar to legitimate cell towers. However, advanced detection tools and methods are being developed to identify and neutralize IMSI catchers.
3.2 Baseband Attacks
Baseband processors in mobile devices handle communication with the cellular network. These processors run their own firmware, which can be vulnerable to exploitation.
-
Exploiting Baseband Processors: Attackers can exploit vulnerabilities in baseband processors to gain control of the mobile device's communication functions. This allows them to intercept calls, SMS messages, and data transmissions.
-
Advanced Techniques: Baseband attacks are highly sophisticated and often require in-depth knowledge of the target device's hardware and software. These attacks are typically carried out by state-sponsored actors or highly skilled hackers.
3.3 Femtocells and Home Network Interception
Femtocells are small cellular base stations used to improve coverage in homes and small businesses. While they offer convenience, they also present security risks.
-
Femtocell Vulnerabilities: Femtocells can be compromised by attackers to intercept calls and data passing through them. Once compromised, a femtocell can be used to conduct MITM attacks or to eavesdrop on communications.
-
Interception via Home Networks: Attackers can also exploit vulnerabilities in home Wi-Fi networks to intercept VoIP calls. Techniques such as ARP spoofing and rogue access points are commonly used to intercept and manipulate traffic on home networks.
3.4 Radio Frequency (RF) Interception
Radio Frequency (RF) interception involves capturing and decoding the radio signals used in mobile communications. This method is often used in military and intelligence operations but can also be employed by malicious actors.
- RF Signal Jamming and Eavesdropping: Attackers can use RF jammers to disrupt legitimate communication channels, forcing mobile devices to communicate on less secure frequencies. They can then use RF eavesdropping equipment to intercept and decode these signals.

- Software-Defined Radio (SDR) Attacks: Software-Defined Radio (SDR) technology allows attackers to capture and analyze a wide range of RF signals.